Most website administrators never scan their WordPress site for malware. That’s like going through life, never getting a checkup from a doctor or dentist. It might be OK for a while, but sooner or later, disaster will strike because you weren’t paying attention!
Why Bother to Scan WordPress for Malicious code?
Alexa reported that more than 40,000 WordPress site installations on their top 1 million websites were vulnerable to hackers. Statistics also show that at any given time, about 18 million sites are infected with malware. At least one percent of all hacked websites are running high fevers right now because of a malware cocktail in their theme, plugin, or WordPress core files.
Is your WordPress site one of them? Time to find out using these three tools to scan WordPress for malicious code and malware attacks.
1. Hog the Web’s Free WordPress Site Security Scanner
Similar to how we get ill because of something we ate or a foreign organism cozying up in our bodies, your WordPress website runs a high fever when a plugin or theme injects malicious code into the installation folder. That malicious code can do anything from stealing passwords to taking your WordPress site offline.
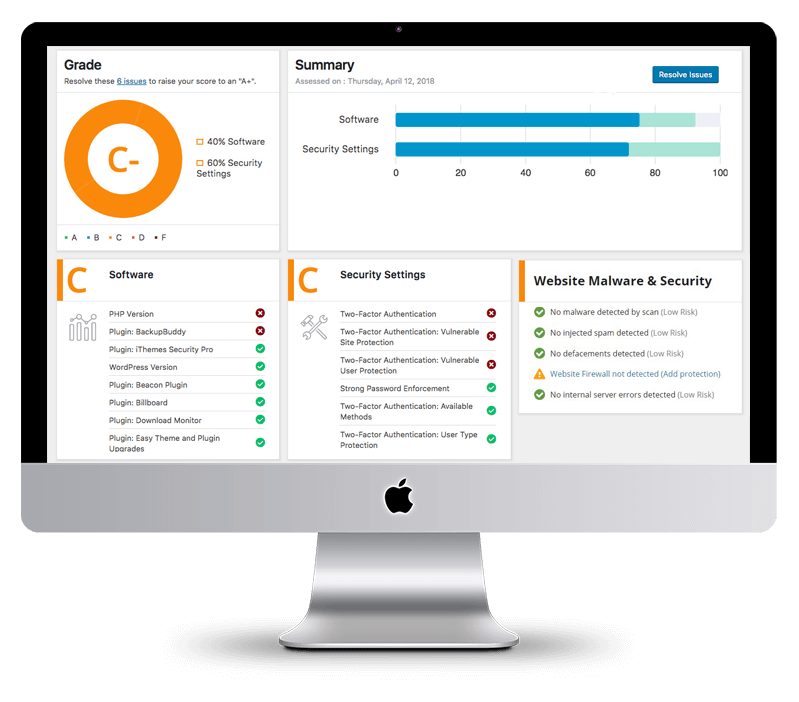
Hog the Web’s free tool goes to the root of all detected malware infections by giving you a way to scan WordPress for malware. It also scans plugins and themes for any malicious code, just like a doctor does blood tests to find out what’s ailing their patient.
With the scanner, you can:
- Check for insecure plugins on WordPress sites
- Check if you’re running an adequate web application firewall
- Check for insecure server configurations
- Search for malware infections using malware detection
- Check your blacklist status
If you were to do a manual security audit of your WordPress site, these are the exact steps you should follow. But it would take a LOT longer to check every line of code on your site’s theme, plugin, and core files manually.
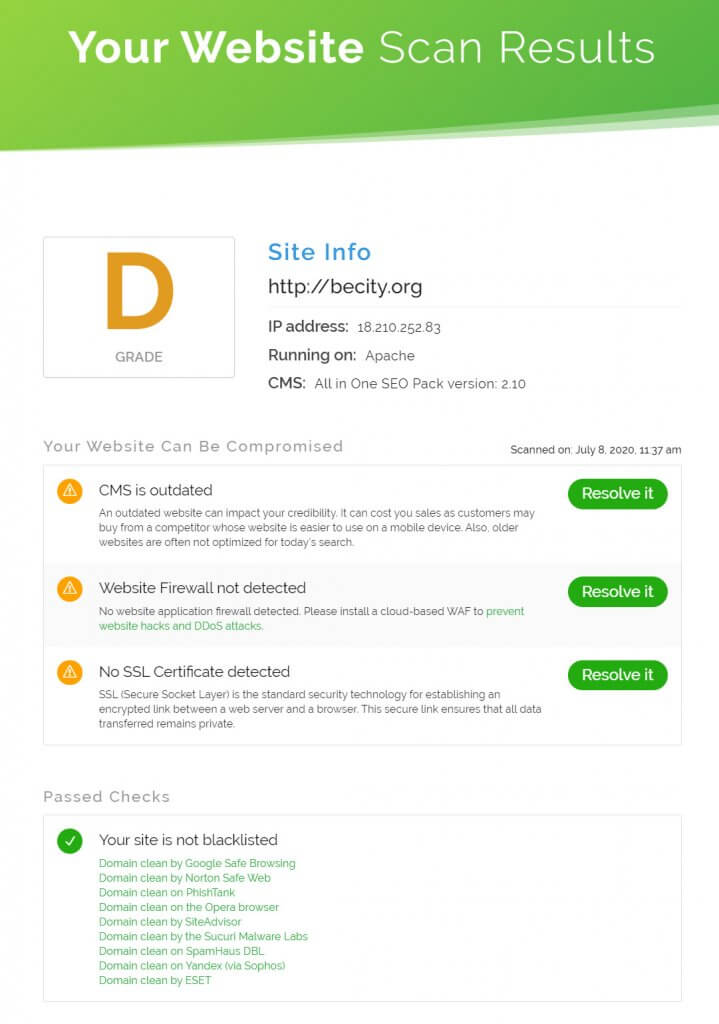
Here’s a preview of the scan results:
The tool sends a detailed report to your email inbox. In the report, you get lots of helpful details on your site’s database scan, along with some tips on how to resolve any security issues.
Right at the top of the report, you get a detailed breakdown of any malware infection that might have infiltrated your WordPress installation. You also get your site’s blacklist status as well as several health diagnostics, like whether you have firewall protection, your server operating system environment, and your WordPress version. Check these out to make sure nothing’s out of date.
Another interesting bit of information worth checking out is the list of internal links and JavaScript files discovered by the tool. If you see any link or file you don’t recognize, that might be a sign of an infection, especially if the links or JavaScript files generate iframes or embed objects on the hacked website.
With Hog The Web’s malware scanner, you get all the information you need to harden your WordPress website against malware attacks.
What really sets this scanner apart from the rest is the accuracy. You don’t get false positives, meaning you won’t be spending hours trying to fix something that’s not broken in the first place.
Anytime you are suspicious about a website’s security or want peace of mind, scan your website with Hog The Web’s free website security scanner for traces of malicious code, just to be safe.
2. PC Risk Website Malware Scanner
The website malware scanner by PC risk, while not dedicated to scanning WordPress specifically for malicious files, does a commendable job of detecting malware. The scanner checks your site for malicious activities, hidden iframes, popular exploit kits, blacklisted status, and infected files.
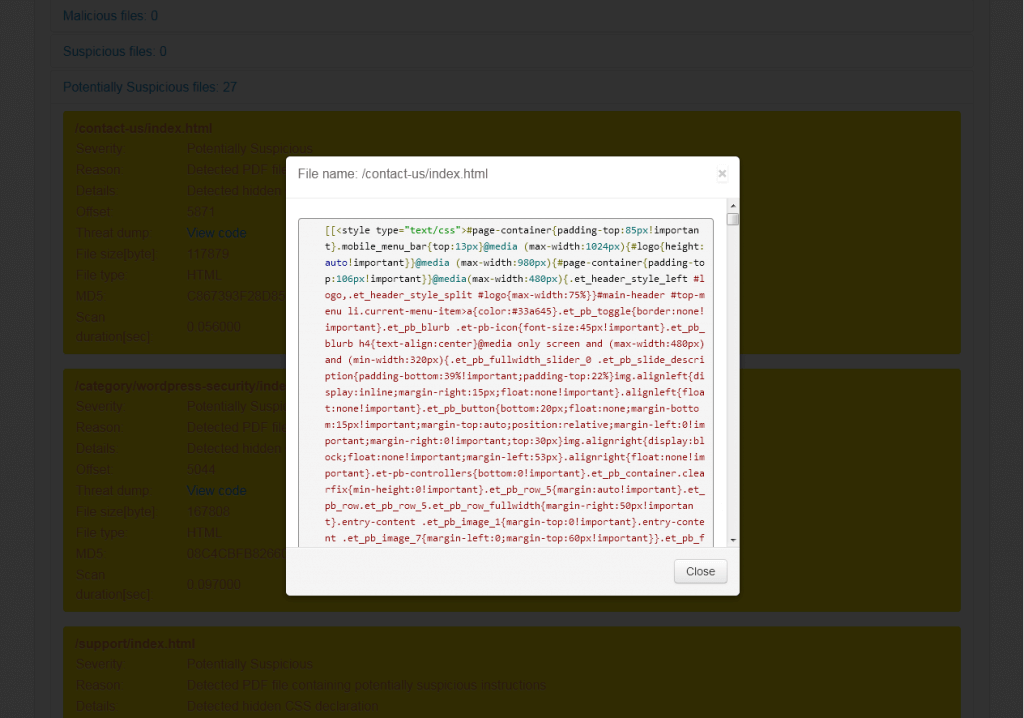
Here’s an example scan from a typical WordPress website; they have 27 potentially suspicious files. Take a look:
That’s a shot of some of the potentially suspicious files uncovered by PC Risk. It shows a PDF file containing potentially suspicious code in the form of a hidden CSS declaration. Let’s dig in further and find out why this hidden CSS declaration is potentially harmful by dumping out the code of one of the infected files.
Here’s the dump from the Contact Us Page that PC Risk reported as having potentially suspicious files:
PC Risk flagged the CSS declaration in the FancyBox plugin on the example site.
We can then check if there are any known security vulnerabilities in the Fancybox plugin within the WordPress Vulnerability Database here. It shows there was one reported vulnerability, but it has since been patched. Since this site uses the latest patched version of the FancyBox plugin, it represents no threat to our site or any other WordPress site.
To conclude, the PC Risk website scanner seems adequate, but you’ll have to deal with a number of false positives as we did. It might report some core WordPress files as potentially malicious or suspicious even when they’re benign. But hey, even Doctors make the occasional misdiagnosis.
3. Foregenix Website Security Scanner
The FGX website security and malware scanner works pretty much like other scanners on this list. All you need to do is enter the URL of the website you want to be checked, hit scan, and wait for the scanner to do its thing.
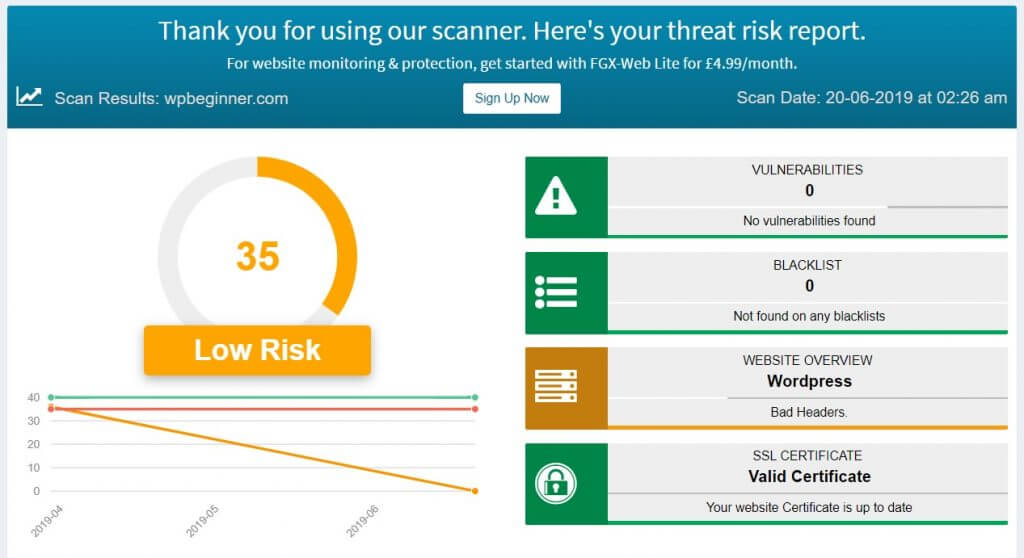
This is the report we got after running a standard WordPress site through Foregenix:
That’s a pretty detailed report. It even shows a website’s historical security status, as you can see on the left part of the report.
Make sure you check the entire report by clicking on the tabs on the left side of your screen after using Foregenix. After running the check on this example site, Foregenix didn’t find anything wrong with the WP configuration, core files or the plugins and theme files I used. It did, however, point out a couple of bad headers.
The Foregenix malware scanner works on numerous websites apart from WordPress sites. So even if you’re running a custom CMS, you can still get a security report with Foregenix. The report might not be as accurate, especially if you’re running a custom CMS whose code is not open to the public. The scanner can only check whether your site has a valid SSL certificate, whether it is blacklisted, or whether it is susceptible to common attacks like malicious code injection and cross-site scripting. Other than that, you’ll not get a complete health check on your custom CMS site when you use Foregenix.
In Conclusion
As a website administrator, you must be proactive to keep your WordPress sites secure. That means regularly scanning it for security vulnerabilities, malware infection, and any other security threats. That’s the only way you’ll stay a step ahead of hackers determined to turn your WordPress site into a spam-spewing robot.
Remember, running security scans on your WordPress sites might not catch all malware attacks. Some types of malware are so well hidden that even the best security features fail to discover them. Always contact a WordPress Security expert whenever you suspect your site’s been infiltrated, even if the tools above aren’t detecting anything.
Learn the 8 simple steps to keep your website secure in this article.
And don’t forget to check your WordPress website to detect malware here!

Levi is the Founder & CEO of Hog The Web, a web design and WordPress services company delivering high-performance websites since 2015. With over a decade of hands-on experience in building, maintaining, and securing websites, Levi leads his team with a focus on craftsmanship, reliability, and long-term client partnerships. Outside the web world, he’s passionate about nature, sustainable living, and giving back through local non-profits and youth education.